Preemptively reveal exposures
to eliminate incidents before they occur










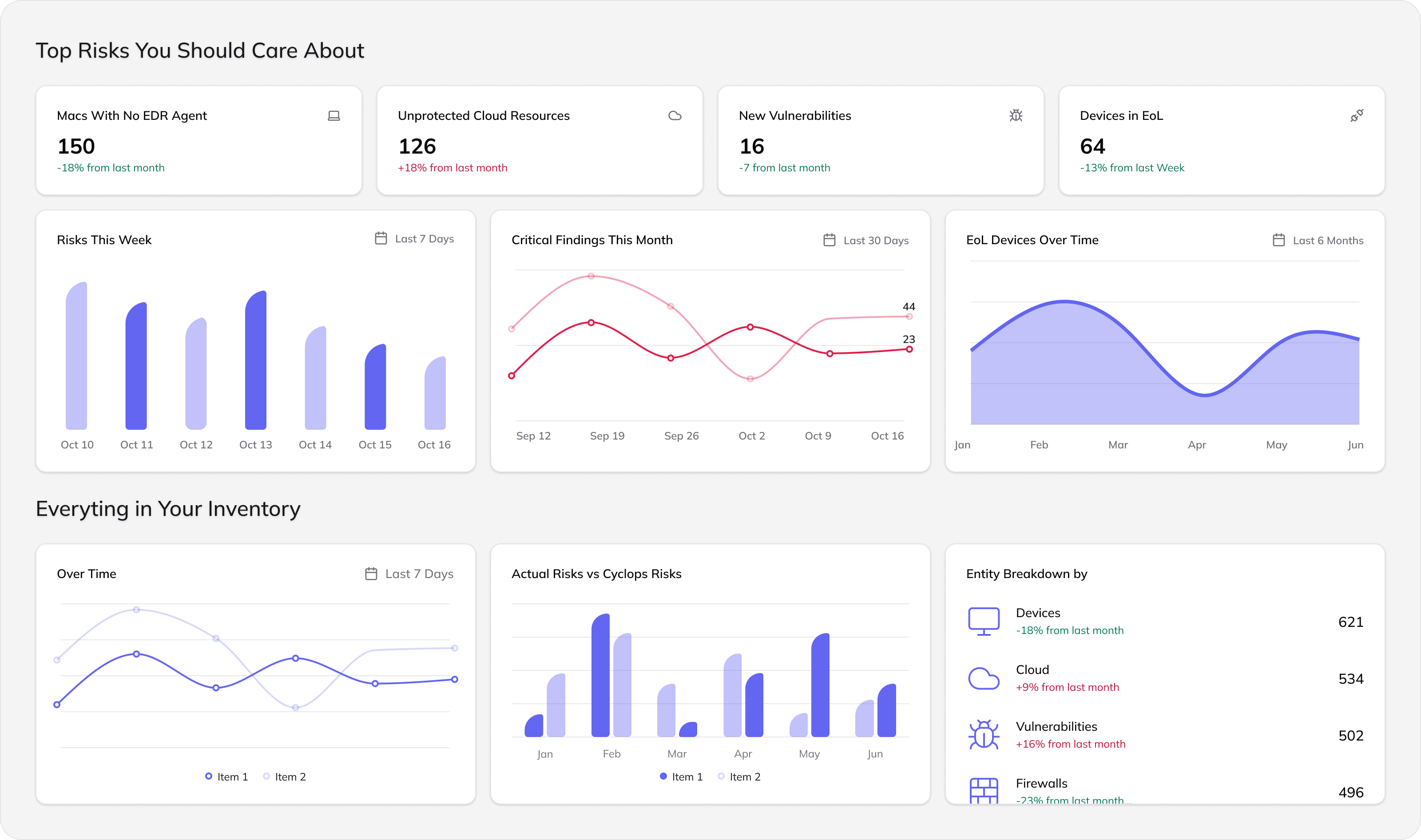
With 150+ integrations and an AI engine, Cyclops merges SaaS, on-prem, and cloud signals into a unified data lake, designed for AI apps.
Chat with an AI agent trained on your data fabric to uncover and understand your risks
Today's data systems weren't built for AI. Cyclops is. We turn fragmented security data into AI-ready intelligence - the foundation for the next generation of security applications.
All your tools, assets, and identities - merged into one lake.
See the correlations that create real-world risk.
Know what to fix first, why and how - with AI guidance.
Connect your stack. See your exposures. Act with confidence.